Explore ultimate online security with a Perfect Forward Secrecy VPN. Learn how this advanced protocol ensures the confidentiality of your encrypted sessions.
For anyone who doesn’t know, Perfect Forward Secrecy (PFS), commonly known as Forward Secrecy, is a critical concept in the realm of digital security, especially regarding VPNs. It's a security protocol that ensures the confidentiality of encrypted sessions, even if the session key is compromised in the future. The Perfect Forward Secrecy VPN uses this protocol to protect online activities, offering a more robust level of security compared to traditional methods by generating unique session keys for each session, meaning that even if one key is compromised, past and future communications remain secure.
In this article, you’ll learn what is Perfect Forward Secrecy, how to enable Perfect Forward Secrecy, and discuss what is the best Perfect Forward Secrecy VPN. If you are seeking a more secure and protected online experience, keep on reading.
Perfect Forward Secrecy IPsec is a method of data encryption that greatly enhances online security. Unlike traditional encryption techniques that use a static key, PFS generates a unique session key for each encrypted interaction. This means that even if a key is compromised in the future, past communications remain secure because they were encrypted with a different key.
If you enable Perfect Forward Secrecy, it is particularly beneficial in protecting sensitive online transactions and communications, as it ensures that even if a cyber attacker gains access to a current key, they cannot decrypt past messages, thus safeguarding users' privacy and data integrity over time.
How to enable Perfect Forward Secrecy VPN to make sure it’s working? This is done using key agreement protocols like Diffie-Hellman, where both parties contribute to creating a unique session key. If a cyber attacker manages to compromise the current key, they can't decrypt past sessions because those were encrypted with different keys.
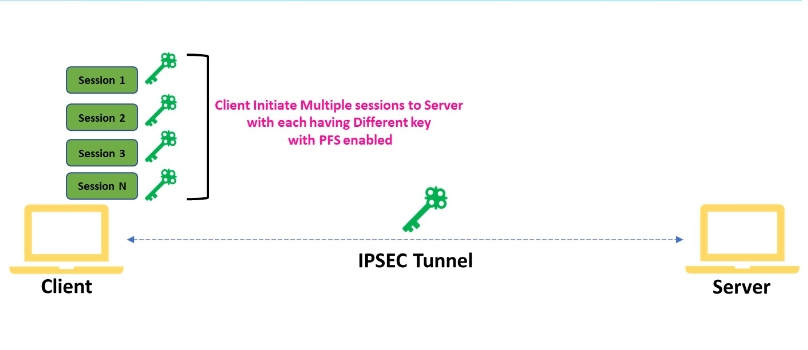 This process of continuously changing keys ensures that even if an encryption key is compromised, previous online activities and data exchanges remain secure. By implementing this protocol, the Perfect Forward Secrecy VPN provides an additional layer of security, making it exceptionally difficult for attackers to access historical data, thereby significantly enhancing user privacy and data protection.
This process of continuously changing keys ensures that even if an encryption key is compromised, previous online activities and data exchanges remain secure. By implementing this protocol, the Perfect Forward Secrecy VPN provides an additional layer of security, making it exceptionally difficult for attackers to access historical data, thereby significantly enhancing user privacy and data protection.
Now we can talk about some real practice after all the introductions. What are the VPNs in the market that are implemented with PFS? To name some notable ones, Proton VPN and ExpessVPN are the top Perfect Forward Secrecy VPN choices you don’t want to miss.
ProtonVPN's PFS protocol employs strong cryptographic principles, making it extremely challenging for unauthorized parties to compromise user data. It operates by using the Diffie-Hellman key exchange protocol to enable both the user's device and the VPN server to collaboratively generate a unique session key for each session, as we mentioned above.

Advantages of ProtonVPN's PFS implementation include:
Enhanced Security: ProtonVPN is designed to enable Perfect Forward Secrecy and ensure that user data remains secure over time. Even if a key is hacked, previous sessions remain confidential. The dynamic key generation process prevents eavesdroppers from intercepting and decrypting users' online activities.
Data Integrity: The Perfect Forward Secrecy with Proton VPN safeguards the integrity of data exchanged during online sessions, preventing unauthorized tampering or modification. You can also benefit from the VPN super unlimited proxy of ProtonVPN.
Privacy Assurance: ProtonVPN's commitment to privacy is further solidified with PFS, as it ensures that past interactions are not vulnerable to surveillance or data breaches.
ExpressVPN is another leading VPN provider that implements Perfect Forward Secrecy to bolster its users' online security and privacy. This Perfect Forward Secrecy VPN also relies on the elliptic curve Diffie-Hellman key exchange, which generates a unique session key for each session.

Advantages of ExpressVPN's PFS implementation:
Dynamic Key Generation: ExpressVPN's use of PFS ensures that keys are continuously generated, providing a high level of security. This prevents attackers from decrypting past sessions even if they compromise a key.
Privacy Protection: Users can trust that their online activities remain private and secure, as ExpressVPN's PFS implementation safeguards against unauthorized access to historical data.
Cross-Platform Compatibility: ExpressVPN offers PFS across various devices and platforms, ensuring a consistent and secure browsing experience for users. If you are seeking streaming VPN free, this one is good to go.
While iTop VPN doesn't feature Perfect Forward Secrecy, its robust encryption protocols make it an exceptional choice for bolstering online privacy. The primary encryption protocol utilized by iTop VPN is the Advanced Encryption Standard (AES) with a key length of 256 bits, commonly known as AES-256.
Here's a breakdown of why iTop VPN stands out as the most secure VPN:
AES-256 Encryption: iTop VPN employs military-grade AES-256 encryption, ensuring the highest level of data security. This military-grade encryption standard is widely recognized for its strength and is considered virtually impenetrable, providing a secure and private environment for online activities.
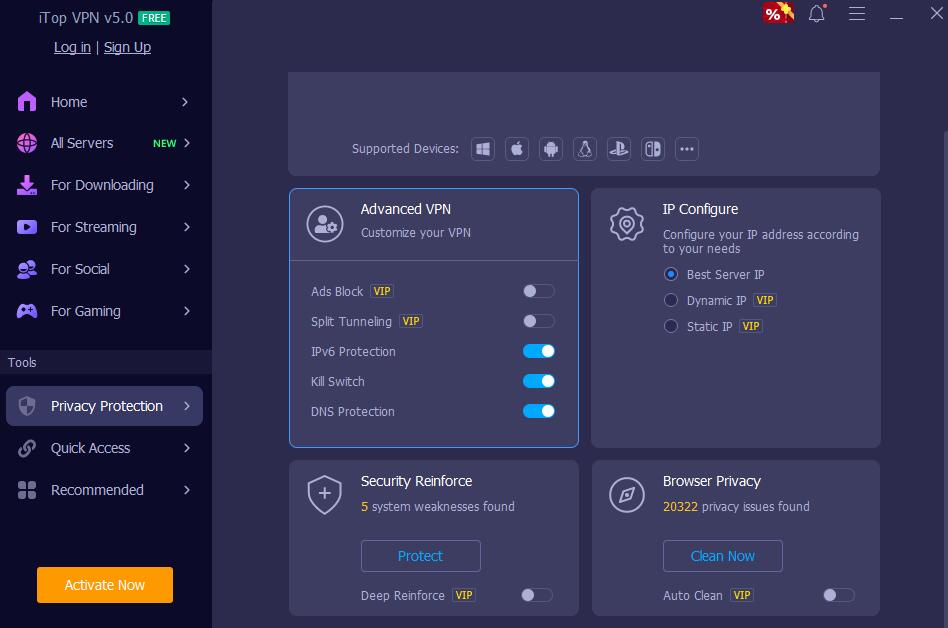
Kill Switch and Split Tunneling: This free VPN for PC includes a Kill Switch that’s able to instantly cut off internet access if the VPN connection drops, preventing any data leaks. Moreover, Split Tunneling allows you to choose which data goes through the VPN, providing flexibility without compromising security.
DNS/IPv6 Protection: iTop VPN ensures DNS and IPv6 protection, shielding against potential leaks that could compromise your privacy. This feature safeguards your online identity by preventing your DNS requests and IPv6 address from being exposed with this free VPN.
No-Log Policy: With a strict no-log policy, iTop VPN guarantees that it does not store any user activity or connection logs, making it the most secure VPN. Your online activities remain confidential, providing you with the peace of mind that your data is not being tracked or recorded.
Encrypted 1800+ Servers: As the best free VPN to change location, iTop VPN operates a vast network of 1800+ servers globally, strategically placed to optimize speed and performance. Each server is encrypted, ensuring a secure connection while offering a seamless browsing experience.
How to Protect Your Online Security and Privacy with iTop VPN:
Step 1: Free download the software compatible with your device. So far, iTop VPN works well with Windows PC, Mac, and iOS. Follow the installation instructions, then launch the iTop VPN application.
Step 2: Choose a server location from iTop VPN's extensive network and establish a secure connection by hitting the Connect button.
Step 3: Explore iTop VPN's additional security features, such as Kill Switch and Split Tunneling, to customize and enhance your online privacy.You can find them all in Privacy Protection.
Q1: Should I enable perfect forward secrecy?
Absolutely. Enabling perfect forward secrecy enhances your security by ensuring that past encrypted sessions remain secure even if your private key is compromised.
Q2: How can iTop VPN protect my online privacy?
iTop VPN safeguards your online privacy through robust AES-256 encryption, anonymous browsing, and IP address masking, preventing unauthorized access to your sensitive data.
Q3: Does IKEv2 use PFS?
Yes, IKEv2 supports Perfect Forward Secrecy. In IKEv2, PFS is implemented through the Diffie-Hellman key exchange, where unique session keys are generated for each session to enhance the overall security of the VPN connection.
Conclusion
In conclusion, Perfect Forward Secrecy VPN, exemplified by leading providers like ProtonVPN and ExpressVPN, ensures that even if encryption keys are compromised, past and future communications remain confidential. However, if you are looking for the ultimate way to online security, iTop VPN merges as the best solution, thanks to its military-grade AES-256 encryption, Kill Switch, Split Tunneling, DNS/IPv6 protection, and a strict no-log policy. Download iTop VPN now to experience top-tier online security and privacy.
10+ free servers in US, UK...
3200+ extensive servers
Dedicated IP addresses
Ad blocker and Proxy service
For Windows 11/10/8/7